网络技术
H3C网络技术
H3C 设备CLI(命令行)管理
H3C基础配置知识
H3C 设备型号概述
H3C网络端口基础信息与配置
H3C网络设备概述
HCL模拟器使用简介
H3C WX2540H 本地portal认证+本地用户认证实现web认证
网络的基本概念与定义
VLAN简介与配置
生成树配置
STP简介与配置
RSTP简介
MSTP基本概念
交换机FTP和TFTP操作
配置文件与升级
网络设备登录管理方式
网络设备文件系统操作
H3C MSR路由器出口双线负载均衡
策略路由配置
以太网链路聚合
DHCP中继
防火墙简单配置实验
华为_HCIP
认识设备-硬件架构与逻辑平面
路由基础-HCIP
OSPF路由基础概述
Router LSA详解
OSPF-Network LSA(二类LSA)与区域内路由计算
OSPF-区域间路由计算
计算机网络-OSPF防环机制
计算机网络-RIP动态路由协议简介
OSPF区域外部路由计算
OSPF特殊区域-Stub区域
计算机网络-NSSA区域与Totally NSSA区域
OSPF路由汇总
OSPF其它特性
IS-IS路由协议基础概念
IS-IS基础概念二
IS-IS邻接关系建立
IS-IS链路状态数据库同步
IS-IS路由计算
IPv6基础概念
IPv6缩写规范与地址分类
ICMPv6基础知识
ICMPv6之NDP协议
计算机网络-IPv6地址配置
DHCPv6基础概念
DHCPv6配置
IPv6路由配置
路由策略与路由工具
计算机网络-Filter-Policy过滤策略
Route-Policy路由策略
策略路由概念与应用
MQC策略简介与配置
流量过滤策略
BGP的背景与概述
BGP基本概念
BGP报文类型简介
BGP状态机制与对等体表项
BGP路由生成与路由表
BGP路由通告原则
BGP基础实验配置
BGP路由优选概述
BGP路由优选原则一Preferred-Value
BGP路由优选原则二-本地优先级
BGP路由优选原则三-路由类型
BGP路由优选原则四-AS_Path属性
BGP路由优选原则五-Origin属性优选
BGP路由优选原则六-优选MED属性值最小的路由
BGP路由优选原则七-EBGP优于IBGP
BGP路由优选原则八-优选IGP Cost值小的路由
BGP路由负载分担
BGP路由反射器与Cluster list选路原则
BGP路由优选原则九-优选Router ID小的设备通告的路由
计算机网络-IP组播基础
组播地址与组播网络组成
组播数据转发原理与RPF
组播分发树与组播协议
IGMP协议简介
IGMPv1工作原理
IGMPv2工作原理简介
IGMPv3的工作原理
IGMP Snooping特性
计算机网络-PIM协议基础概念
PIM-DM密集模式工作原理
基于PIM-DM+IGMP的组播实验配置
PIM-SM(ASM)基础
PIM-SM(SSM)基本原理
PIM-SM组播实验
BFD检测机制
BFD配置实验
VRRP基础概念
VRRP工作原理与选举过程
VRRP主备切换与主备回切
VRRP基础实验一
RSTP基础概念
RSTP工作原理与P/A机制
MSTP概述
MSTP基础概念
MSTP工作原理概述
MSTP基础实验一(单域多实例)
计算机网络-VPN虚拟专用网络概述
计算机网络-GRE(通用路由封装协议)简介
GRE-动态路由协议实验
IPSec VPN基本概念
IPSec VPN工作原理
IPSec VPN基础实验一(主模式)
GRE Over IPSec实验
计算机网络-L2TP VPN基础概念与原理
L2TP VPN基础实验配置
L2TP Over IPSec基础实验
SSH理论基础
VRF基本概念
MPLS基础概念
MPLS转发原理
MPLS静态标签实验
计算机网络-LDP标签分发协议
LDP工作原理-LDP会话建立
LDP标签发布与管理
LDP工作过程详解
VPN实例应用于交换机带外管理接口
H3C V7防火墙IPSECVPN配置(主模式配置)
网络设备拨号设置
网络地址分类与子网划分
防火墙区域以及安全策略配置(命令行版)
H3C V7 IPSEC_VPN配置(野蛮模式配置)
华为_HCIA
路由基础
以太网交换基础
VLAN的原理与配置
VLAN间通信
STP生成树简介
华为VRP系统简介
NAT网络地址转换
ACL访问控制列表
AAA的原理与配置
DHCP配置
链路聚合原理与配置
PPP与PPPoE协议
OSPF路由基础
无线通信基础原理
无线组网基本概念
无线网络配置原理与步骤
典型无线组网实验配置
网络设备防火墙是什么?
防火墙工作原理与安全策略
华为VRP系统基础命令配置
本文档使用 MrDoc 发布
-
+
首页
H3C V7防火墙IPSECVPN配置(主模式配置)
# H3C V7防火墙IPSECVPN配置(主模式配置) 需求:采用两台防火墙搭建IPSECVPN,前提条件将ip地址,域间策略,路由配置好。采用两边主模式进行配置。使得192.168.1.0/24网段和192.168.3.0/24网段能够互相访问。 拓扑图如下: 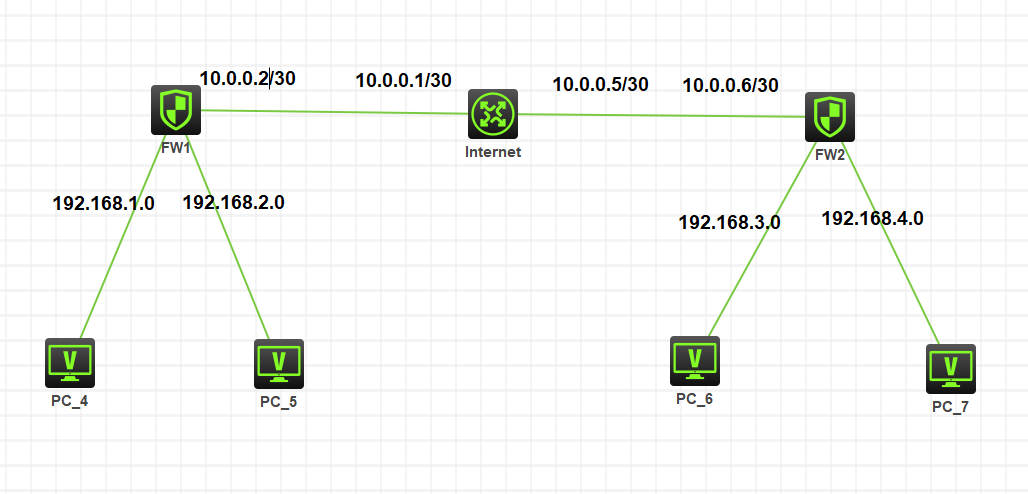 ## 配置 FW1: ```shell # 接口配置 interface GigabitEthernet1/0/0 port link-mode route combo enable copper ip address 10.0.0.2 255.255.255.252 # interface GigabitEthernet1/0/1 port link-mode route combo enable copper ip address 192.168.1.1 255.255.255.0 # interface GigabitEthernet1/0/2 port link-mode route combo enable copper ip address 192.168.2.1 255.255.255.0 # 路由配置 ip route-static 0.0.0.0 0 10.0.0.1 # ACL匹配NAT转换 acl advanced 3000 rule 0 deny ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255 rule 9999 permit ip # 3001匹配感兴趣流 acl advanced 3001 rule 0 permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255 # IPSEC VPN配置 # 配置ike 安全提议,名称为1,指定加密算法和认证算法,两端需要一样 ike proposal 1 encryption-algorithm 3des-cbc authentication-algorithm md5 # 配置IKE keychain,名称为FW2,指定对端地址和预定义共享密钥123456 ike keychain FW2 pre-shared-key address 10.0.0.6 255.255.255.255 key simple 123456 # 定义IKE profile并调用keychain和proposal以及定义对端地址和本段地址 ike profile FW2 keychain FW2 local-identity address 10.0.0.2 match remote identity address 10.0.0.6 255.255.255.255 proposal 1 # 配置ipsec安全提议,采用esp协议,默认为tunnel模式,指定认证协议和加密协议 ipsec transform-set FW1 esp encryption-algorithm 3des-cbc esp authentication-algorithm md5 # 配置ipsec策略,策略名称FW1,序号1,采用isakmp方式 ipsec policy FW1 1 isakmp transform-set FW1 security acl 3001 local-address 10.0.0.2 remote-address 10.0.0.6 ike-profile FW2 # 端口应用ipsec策略 interface GigabitEthernet1/0/0 nat outbound 3000 ipsec apply policy FW1 ``` FW2: ```shell # 接口配置 interface GigabitEthernet1/0/1 port link-mode route combo enable copper ip address 10.0.0.6 255.255.255.252 # interface GigabitEthernet1/0/2 port link-mode route combo enable copper ip address 192.168.3.1 255.255.255.0 # interface GigabitEthernet1/0/3 port link-mode route combo enable copper ip address 192.168.4.1 255.255.255.0 # 路由配置 ip route-static 0.0.0.0 0 10.0.0.5 # ACL匹配NAT转换 acl advanced 3000 rule 0 deny ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 rule 9999 permit ip # 匹配感兴趣流,与对端相反 acl advanced 3001 rule 0 permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 # 配置IKE 安全提议,名称1,定义加密协议和认证协议 ike proposal 1 encryption-algorithm 3des-cbc authentication-algorithm md5 # 配置IKE keychain ike keychain FW1 pre-shared-key address 10.0.0.2 255.255.255.255 key simple 123456 # 配置ipsec安全提议,名称FW2,定义加密协议和认证协议,与对端一致 ipsec transform-set FW2 esp encryption-algorithm 3des-cbc esp authentication-algorithm md5 # 配置IKE profile ike profile FW1 keychain FW1 local-identity address 10.0.0.6 match remote identity address 10.0.0.2 255.255.255.255 proposal 1 # 配置ipsec策略,名称FW2,序号2,isakmp方式,调用安全提议,感兴趣流ACL,profile配置 ipsec policy FW2 1 isakmp transform-set FW2 security acl 3001 local-address 10.0.0.6 remote-address 10.0.0.2 ike-profile FW1 # 接口应用 interface GigabitEthernet1/0/1 port link-mode route combo enable copper ip address 10.0.0.6 255.255.255.252 nat outbound 3000 ipsec apply policy FW2 ```
Chuck
2022年8月4日 14:32
转发文档
收藏文档
上一篇
下一篇
手机扫码
复制链接
手机扫一扫转发分享
复制链接
Markdown文件
分享
链接
类型
密码
更新密码